Nmap Port Scan Analysis
By Farhan Ahmed – Jun 19, 2023
Nmap, short for “Network Mapper,” is a powerful and versatile network scanning tool widely used by security professionals, network administrators, and ethical hackers. It provides a comprehensive means of exploring and auditing network hosts, identifying open ports, services, and operating systems running on those hosts, and detecting potential vulnerabilities. Nmap operates by sending carefully crafted packets to target systems and analyzing the responses received. It supports a wide range of scanning techniques, including TCP, UDP, SYN, ACK, and ICMP scans, allowing users to gain insights into network topology, discover hosts, and assess the security posture of their network infrastructure. Nmap’s flexibility, robustness, and extensive feature set make it an essential tool for both offensive and defensive network security purposes.
TCP: First we scan a host 172.16.0.1 using TCP ports utilizing nmap in the Ubuntu Terminal:
root@laboratorio:~# nmap 172.16.0.1 -p 1-100 -v
Starting Nmap 5.21 ( http://nmap.org ) at 2014-11-17 13:34 CET
Initiating ARP Ping Scan at 13:34
Scanning 172.16.0.1 [1 port]
Completed ARP Ping Scan at 13:34, 0.02s elapsed (1 total hosts)
mass_dns: warning: Unable to open /etc/resolv.conf. Try using –system-dns or specify valid servers with –dns-servers
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using – -system-dns or specify valid servers with –dns-servers
Initiating SYN Stealth Scan at 13:34
Scanning 172.16.0.1 [100 ports]
Discovered open port 7/tcp on 172.16.0.1
Discovered open port 37/tcp on 172.16.0.1
Discovered open port 9/tcp on 172.16.0.1
Discovered open port 13/tcp on 172.16.0.1
Discovered open port 19/tcp on 172.16.0.1
Completed SYN Stealth Scan at 13:34, 1.11s elapsed (100 total ports)
Nmap scan report for 172.16.0.1
Host is up (0.00053s latency).
Not shown: 95 closed ports
PORT STATE SERVICE
7/tcp open echo
9/tcp open discard
13/tcp open daytime
19/tcp open chargen
37/tcp open time
MAC Address: E8:39:35:3C:DB:87 (Unknown)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.18 seconds
Raw packets sent: 108 (4750B) | Rcvd: 101 (4062B)
UDP: The same procedure is repeated for UDP port in the following manner:
root@laboratorio:~# nmap 172.16.0.1 -p 1-100 -sU –v
Starting Nmap 5.21 ( http://nmap.org ) at 2014-11-17 13:34 CET
Initiating ARP Ping Scan at 13:34
Scanning 172.16.0.1 [1 port]
Completed ARP Ping Scan at 13:34, 0.01s elapsed (1 total hosts)
mass_dns: warning: Unable to open /etc/resolv.conf. Try using –system-dns or specify valid servers with –dns-servers
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using – -system-dns or specify valid servers with –dns-servers
Initiating UDP Scan at 13:34
Scanning 172.16.0.1 [100 ports]
Increasing send delay for 172.16.0.1 from 0 to 50 due to max_successful_tryno increase to 4 Increasing send delay for 172.16.0.1 from 50 to 100 due to max_successful_tryno increase to 5
Increasing send delay for 172.16.0.1 from 100 to 200 due to max_successful_tryno increase to 6
Increasing send delay for 172.16.0.1 from 200 to 400 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 172.16.0.1 from 400 to 800 due to 11 out of 11 dropped probes since last increase.
UDP Scan Timing: About 48.75% done; ETC: 13:35 (0:00:33 remaining)
Discovered open port 13/udp on 172.16.0.1
Discovered open port 7/udp on 172.16.0.1
Discovered open port 19/udp on 172.16.0.1
Completed UDP Scan at 13:36, 100.86s elapsed (100 total ports)
Nmap scan report for 172.16.0.1
Host is up (0.00058s latency).
Not shown: 96 closed ports
PORT STATE SERVICE
7/udp open echo
9/udp open|filtered discard
13/udp open daytime
19/udp open chargen
MAC Address: E8:39:35:3C:DB:87 (Unknown)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 100.93 seconds
Raw packets sent: 225 (6330B) | Rcvd: 105 (5882B)
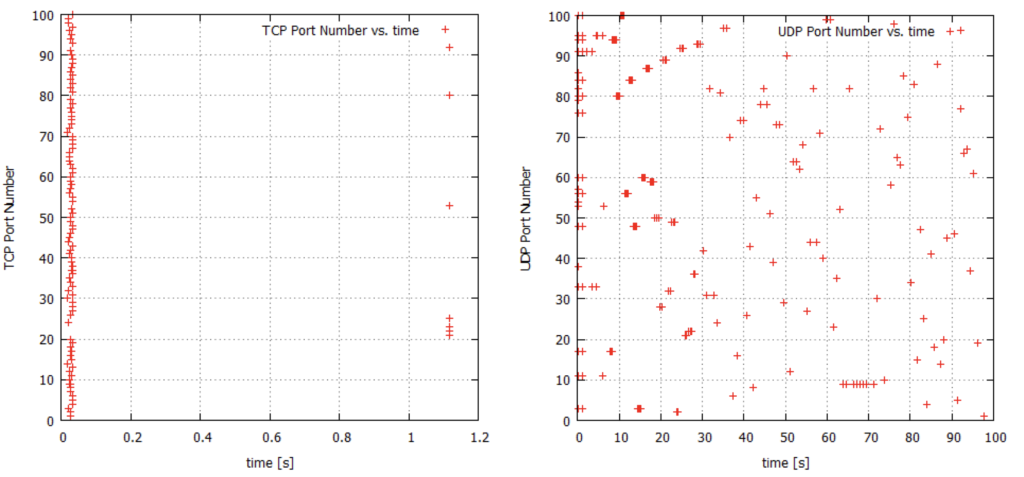
Analysis: It is observed that from the plots and wireshark capture, TCP scan (1.18s) is much faster than UDP scan (100.93s). In the TCP capture, the TCP SYN packets are sent collectively for many ports and similarly the target host sends collective TCP RST packets to assert that the target port is closed for example, Nmap sends SYN packet to the first 42 randomly scanned ports in the beginning and each port replies once. Thus in case of TCP nmap checks each port once at a time, so that the time taken to completely scan 100 ports is around 1.1 seconds. It is interesting to note that Nmap does the scan in two batches as evident in the TCP graph.
Whereas the UDP scan is much slower than TCP. The reason can be verified by looking at the plot and UDP’s wireshark capture. Those ports which are closed or filtered, send a Destination unreachable (port unreachable) ICMP packet and the time to send this message is slow, as if there is a limit to the rate of ICMP messages with time. Furthermore UDP behaves differently as TCP, collective packets are sent at the start and after some time, no collective packets are sent. Also UDP is a connectionless protocol so you are never sure whether you will even receive an ICMP unreachable message or not and hence multiple packets are sent to the same port number. Since there are many ports which are closed, hence time taken to completely scan 100 ports is around 100 seconds.
Latest Posts

